🕵️ I tested 5 Leaked Password Checkers – Here's What I Found
Sometimes you end up uncovering things about your passwords you never even imagined.
There are countless systems out there claiming to tell you if your passwords have been leaked. But not all of them show you exactly which password was exposed or where the breach happened. Sometimes, you need to do a bit of digging and data cross-referencing to figure that out.
I tested a few of the services currently available.
Check out the results below.
This isn’t a ranking, and there are probably other tools I haven’t come across yet, so your input will be key.
Have I Been Pwned?
This is one of the most well-known services. It tells you where breaches occurred and what types of data were exposed, but it doesn’t clearly show the exact information—leaving it up to the user to dig into each platform for more details.
One useful feature is the alerts. They offer a free service called “Notify Me” that monitors your email, and if it shows up in a breach, you get notified by email.
https://haveibeenpwned.com/
Mozilla Monitor
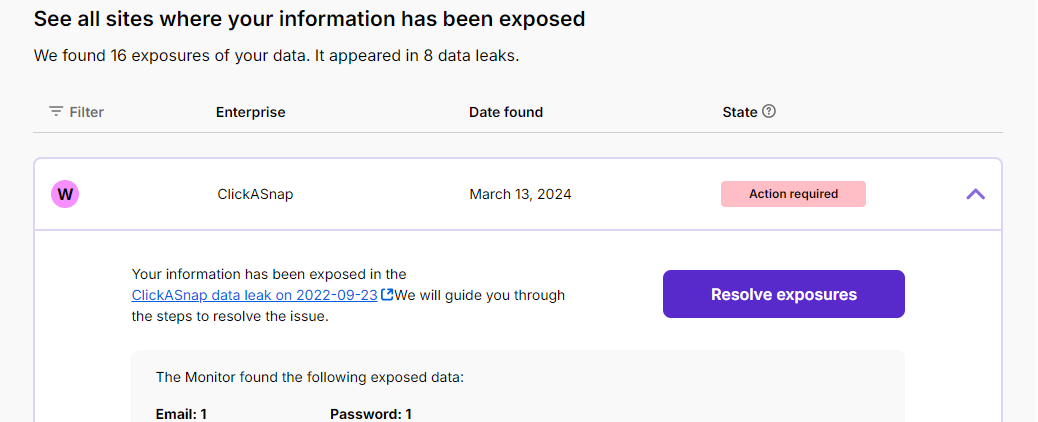
It also sends alerts and presents the breach information in a very user-friendly way—showing the source, date, origin, and exactly which types of data were exposed, along with how many. It works really well.
In the test above, for example, I discovered a ClickASnap breach that Have I Been Pwned hadn’t flagged. So, it’s a good reminder: relying on just one service isn’t always enough.
https://monitor.mozilla.org/
Other similar services:
Avast Hack Check
Dehashed
No Chrome, revise as senhas com chrome://password-manager/checkup?start=true
https://amibreached.com/
https://leakcheck.io/
IntelX - https://intelx.io
Scatteredsecrets
Scattered shows you the actual password that was leaked, not just a vague alert saying your password was compromised and leaving you to guess which one you were using at the time of the breach.
It’s a great service with low pricing for personal use, plus a free version. The passwords it showed were exactly the ones I used at the time, so you can tell it’s quite accurate.
https://scatteredsecrets.com/
Google - Dark web Report
Did you know that Google offers this service for free for personal accounts (@gmail.com)?
I tested it with my own email and got very detailed results, including indications of which passwords or data had been exposed.
Now let’s check some more IT engines:
TorBot - Crawler
Check out TorBot: https://owasp.org/www-project-torbot/
To get started, you can spin up an Ubuntu VM (if you’re not already using Linux) and run the following commands:
sudo apt update && sudo apt upgrade -y
sudo apt install git python3 python3-pip tor -y
sudo apt install python3-venv curl -y
sudo apt install python3.10
python3.10-venv -y
git clone https://github.com/DedSecInside/TorBot.git
cd TorBot
python3.10 -m venv .venv
source .venv/bin/activate
pip install -r requirements.txt
sudo service tor startTo check if Tor is running properly:
curl --socks5 127.0.0.1:9050 https://check.torproject.orgYou should see a message confirming that you're using Tor. If not, a dependency might be missing—double-check your Python version and environment.
Go to the /TorBot/scripts/ directory and run the install.sh script.
Done. With TorBot installed, you’ll be able to run crawlers and scan .onion sites on the deep web for emails, personal data, and other exposed information.
Here’s an example command:
python3 torBot.py -u https://duckduckgogg42xjoc72x3sjasowoarfbgcmvfimaftt6twagswzczad.onion -m -sIn this case, it searches DuckDuckGo on the Tor network, but you can use any other site as well.
DarkDump
Darkdump is a Python-based OSINT tool for conducting investigations on the deep web. It lets users enter a search query and then crawls related .onion sites, attempting to extract emails, metadata, keywords, images, social media accounts, and more. Darkdump retrieves sites via Ahmia.fi and accesses these .onion addresses when connected to the Tor network.
I tested it using Python 3.8. Searches take a bit longer since they're performed live.
git clone https://github.com/josh0xA/darkdump
cd darkdump
python3 -m pip install -r requirements.txt
python3 darkdump.py --helpYou’ll need to configure the Tor network hash—see instructions here: https://github.com/josh0xA/darkdump
Example search commands:
Search for 10 links and extract all content from the found sites:
python3 darkdump.py -q "keyword" -a 10 --scrape --proxySearch for 25 links without scraping (Tor not required):
python3 darkdump.py -q "keyword" -a 25In the example below, it was easy to find where data was being sold. First, you can use Darkdump to look up group or site names involved in data breaches, and then use the Tor browser to explore the details.
And what about you ? Do you recommend some tool or website to monitor or find data leaks?














Love this site - have I been pwnd.