💸 How Your Data Is Sold on the Dark Web?
An investigation into the ilegal market for personal information and how data leaks end up in the hands of criminals.
Have you ever wondered what happens to your data after a leak? Hint: it doesn’t just vanish! It becomes a commodity on the dark web. In this article, I explore how this underground trade actually works , from data collection to sale and payment, exposing the mechanics that keep this market running.
Or did you think asking Google to delete your data was enough?
I decided to write this piece because many people commented on my last post asking to know more about the dark web and how to “exercise their rights” there… spoiler: don’t get your hopes up.
So I’m structuring this post like stages or chapters , whichever term you prefer. I kept it concise to avoid making this post massive, since this topic alone could easily fill an entire course.
Note: This article is based on publicly available information and is intended for educational purposes only. We do not endorse or encourage any illegal activity or access to dark web content.
What Are the Deep Web and the Dark Web?
I’m not expecting all readers here to be experts in the field, so a quick explanation is a good start.
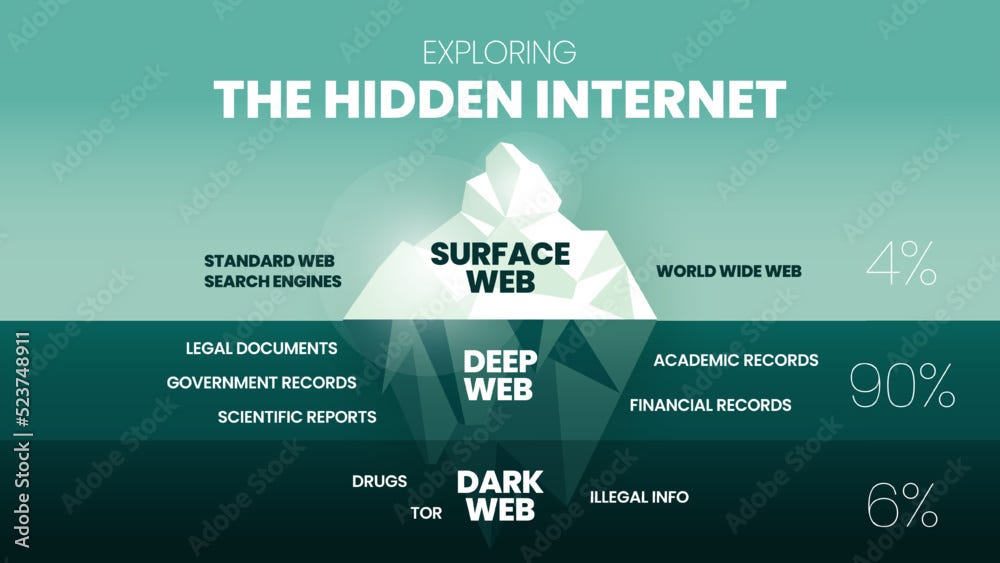
The internet we use every day is just the tip of the iceberg. This visible layer, known as the Surface Web, includes websites indexed by search engines like Google and Bing. But beneath that surface lies a much larger universe that's hidden from view.
The Deep Web includes all web pages that aren't indexed by search engines. It's estimated to account for over 90% of all online content. This layer hosts legitimate information such as academic databases, medical records, online banking portals, private emails, and any content protected by passwords or paywalls. For example, when you log into your online bank account, you're accessing the Deep Web.
The Dark Web, on the other hand, is a small portion of the Deep Web that is intentionally hidden and only accessible through specific software, such as the Tor Browser. Addresses in this layer usually end with the ".onion" domain and consist of random strings of letters and numbers that don’t make immediate sense. Tor (The Onion Router) uses multiple layers of encryption and a network of relays to anonymize traffic, making it extremely difficult to trace the origin and destination of connections.
“The Dark Web hosts a wide range of content, from legitimate activities to highly illegal ones,” explains a digital security expert. Among the legitimate uses are forums for activists in authoritarian countries, platforms for investigative journalism, and secure channels for military communication. However, the anonymity it provides also attracts criminal activity , including drug trafficking, arms sales, and the focus of this investigation: the trade of stolen personal data.
Step 1 – Data Capture
The journey of leaked data to the Dark Web begins with its illegal acquisition. This can happen through cyberattacks on companies and government agencies, exploitation of system vulnerabilities, social engineering, or even the involvement of corrupt insiders with privileged access to databases.
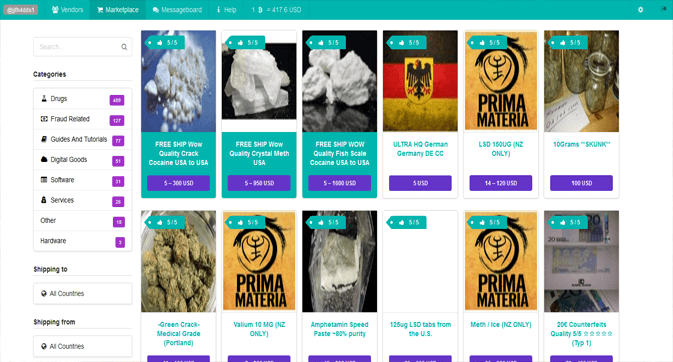
Once stolen, the data is sorted, categorized, and listed on specialized Dark Web marketplaces. These platforms operate surprisingly like regular e-commerce sites, with vendor ratings, reputation systems, and even customer support.
The data market on the Dark Web revolves around two main types of actors: legitimate and illegal data brokers. Legitimate data brokers are companies that legally collect, analyze, and sell personal information, though their practices are often controversial. Illegal brokers operate exclusively in the Dark Web, trading data obtained through breaches and hacks.
The process usually begins with one of the following methods:
Malware and infostealers: malicious software that infects devices and extracts personal information.
Phishing: deceptive techniques used to trick victims into handing over login credentials and sensitive data.
Corporate data breaches: security failures that expose large volumes of information , a topic we've covered frequently in this newsletter.
During my investigation, I came across listings for "hacking on demand" services, where cybercriminals advertise their skills to target specific systems.
One such ad, on a site called "Rent-A-Hacker," offered services like hacking email accounts, social media profiles, websites, and even organizations. Prices ranged from €250 to €1,000 depending on the job’s complexity. The seller promised full anonymity and accepted payments exclusively in Bitcoin.
This data is then organized and prepared for sale on specific marketplaces within the dark web.
Step 2 – Where to Sell?
There are several forums and marketplaces on the dark web dedicated to selling stolen data, including:
Genesis Market: specialized in selling "bots" that contain full profiles from infected devices, including cookies and login credentials.
2easy: known for trading logs extracted from malware, offering detailed user information.
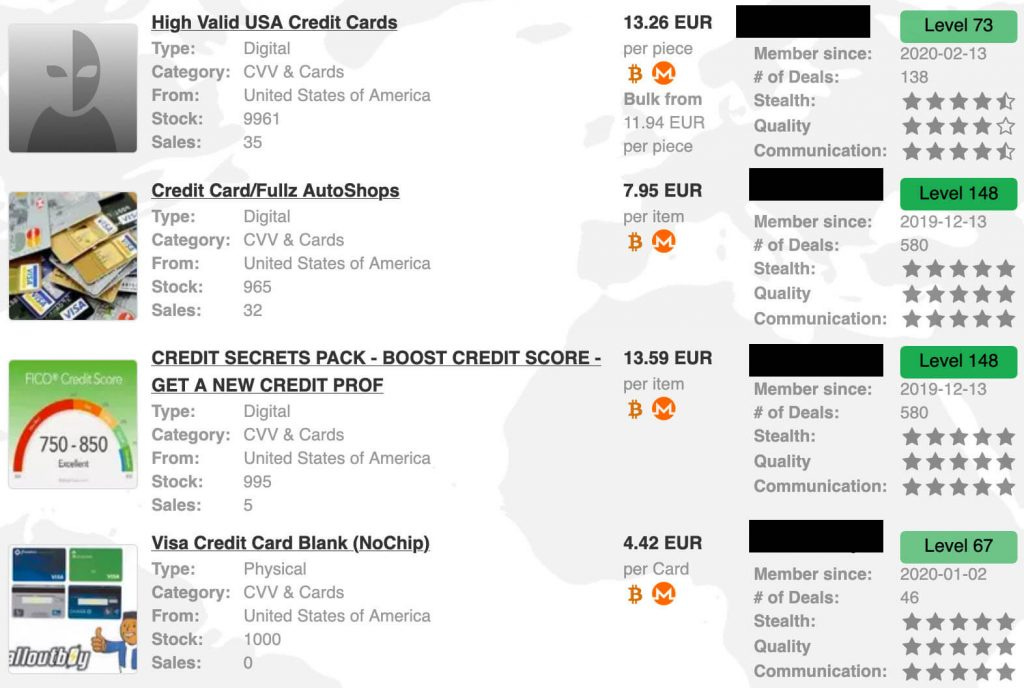
BidenCash: focused on the sale of credit card data and personal information.
These marketplaces operate much like e-commerce platforms, featuring reputation systems for sellers and search filters for data types or country of origin.
Step 3 – How Payments Are Made
Transactions in these markets are typically carried out using cryptocurrencies like Bitcoin or Monero to preserve anonymity. While Bitcoin isn’t truly anonymous, those who know how to operate in P2P networks with trusted contacts can stay well under the radar.
Direct payments: cryptocurrency is sent straight to the seller’s wallet.
Escrow services: the buyer sends the payment to a trusted intermediary, who only releases the funds to the seller after confirming delivery of the data.
Automated Shops (Autoshops): fully automated platforms where buying and delivering data happens without human interaction, increasing efficiency and lowering risks for criminals.
Monero uses technologies like ring signatures, stealth addresses, and confidential transactions to hide the origin, destination, and amount of each transfer , making it an increasingly preferred option for illicit activities.
To boost anonymity even further, dark web users often turn to services known as “mixers” or “tumblers.” These services blend cryptocurrencies from multiple sources before sending them to their final recipients, making it much harder to trace the origin of the funds. One ad found during our investigation promised: “Our mixing service guarantees 100% anonymity. Your bitcoins will be completely clean after passing through our system.”
On one of the forums we analyzed, an admin had posted the following warning: “All transactions over 0.05 BTC must use our escrow service. We won’t accept complaints from users who ignore this rule and get scammed.”
Step 4 – The Value of Data
The price of data depends on the type and quality of the information:
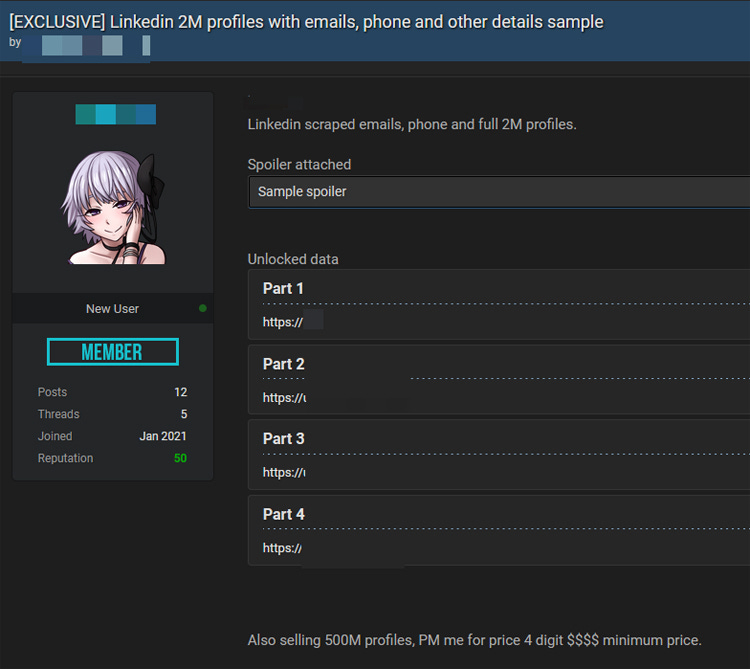
Social media login credentials: typically sold for $10 to $50.
Credit card data: prices range from $20 to $200, depending on the credit limit and location.
Full identity packages (including credit history): usually go for $60 to $100.
Full identity information (name, address, documents, etc.): these complete packages can fetch higher prices, especially if they belong to citizens of developed countries, high-income individuals, or public figures.
Health data: depending on the person and the amount of information, it can sell for over $500 per individual. For example, medical records of a well-known person who was recently hospitalized are often auctioned to the highest bidder.
During a visit to one of the most well-known marketplaces on the Dark Web, I came across listings offering data packages containing millions of Brazilian records. One of them, titled “Brasil Full Package 2023”, offered complete information on over 50 million citizens, including name, documents, address, phone number, email, banking details, and credit history, for 0.35 Bitcoin (around R$120,000 at current exchange rates).
Step 5 – Who’s Buying?
The end buyers of this data are criminals who use it for a variety of illicit purposes. With full personal information, they can create fake identities, open fraudulent bank accounts, apply for loans, make online purchases, and carry out targeted scams. A common tactic is sending fake invoices that appear legitimate because they contain accurate personal details about the victim.
This ecosystem is supported by a range of auxiliary services, including crypto laundering, fake document creation, malware development, and fraud consulting. During the investigation, I found forums entirely dedicated to sharing methods for monetizing stolen data, complete with detailed tutorials on how to execute different types of scams.
The sale of personal data on the dark web poses a serious threat to privacy and digital security. With this information, criminals can commit financial fraud, shop or apply for loans in the victim’s name, steal identities, generate fake documents, access restricted services, and launch targeted attacks like spear phishing , using personal details to make the scams more convincing.